The Kimwolf Botnet: A Massive Threat Lurking in Your Living Room


The Kimwolf Botnet: How 1.8 Million Smart TVs Became a Cyber Weapon
In the ever-evolving landscape of cybersecurity threats, few developments in late 2025 have been as alarming as the emergence of the Kimwolf botnet. Discovered by researchers at QiAnXin XLab, this hyper-scale Android-based malware network has infected an estimated 1.8 million devices worldwide—primarily smart TVs, set-top boxes, and tablets. What makes Kimwolf particularly dangerous is its sheer size, sophisticated evasion techniques, and potential for devastating DDoS attacks approaching 30 Tbps in power.
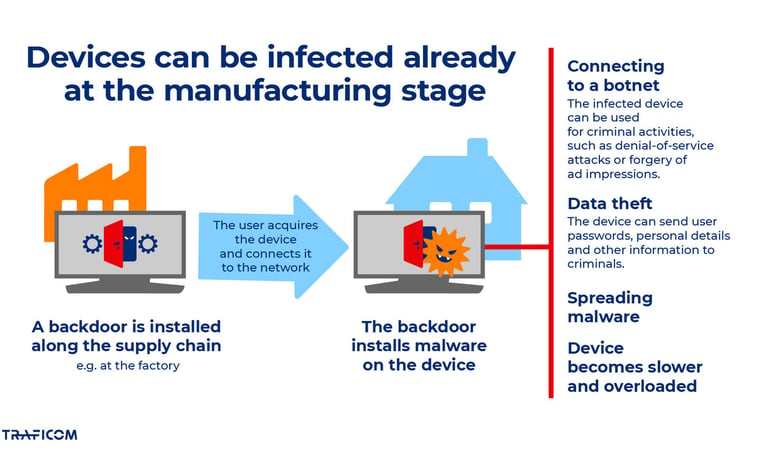
This botnet isn't just a technical curiosity; it's a wake-up call for anyone with connected devices at home. Many infections stem from cheap, uncertified Android TV boxes that come pre-loaded with malware or are easily compromised due to lack of updates.
Discovery and Rapid Growth
QiAnXin XLab first encountered Kimwolf on October 24, 2025, when a security partner submitted a suspicious sample. The malware's command-and-control (C2) domain quickly skyrocketed in traffic, briefly surpassing Google to rank #1 on Cloudflare's global domain popularity list in November.
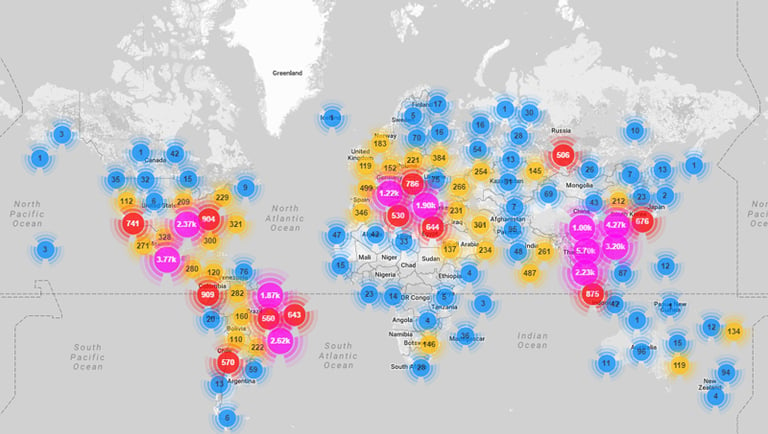
By early December, sinkhole data revealed the botnet's true scale: over 2.7 million unique IPs in just three days, with peak active bots reaching 1.83 million on December 4. Infections span 222 countries, concentrated in Brazil, India, the United States, Argentina, South Africa, and the Philippines.
By early December, sinkhole data revealed the botnet's true scale: over 2.7 million unique IPs in just three days, with peak active bots reaching 1.83 million on December 4. Infections span 222 countries, concentrated in Brazil, India, the United States, Argentina, South Africa, and the Philippines.
Technical Breakdown: How Kimwolf Works
Kimwolf is a native Android malware compiled with the Android NDK, integrating the wolfSSL library (hence the name). It spreads mainly through pre-installed or sideloaded APKs on generic TV boxes like SuperBOX, X96Q, and MX10—devices often sold as "fully loaded" with pirated content.
Key capabilities include:
13 DDoS attack methods (UDP, TCP, ICMP floods, etc.)
Residential proxy forwarding (likely monetized by renting out infected IPs)
Reverse shell and full file management for remote control
In one three-day period (November 19–22), it issued a staggering 1.7 billion DDoS commands. Researchers confirmed its involvement in a near-30 Tbps attack on December 9.
Here's a classic illustration of how botnets like Kimwolf orchestrate DDoS attacks:
Advanced Evasion and Resilience
What sets Kimwolf apart is its adaptability. After at least three C2 domain takedowns in December, operators shifted to Ethereum Name Service (ENS) and "EtherHiding" techniques—using blockchain smart contracts for unbreakable C2 resolution. They even taunted researchers with messages like "we have 100s of servers keep trying LOL!"
Other defenses:
DNS-over-TLS (DoT) for encrypted queries
ECDSA signatures to verify legitimate commands
String obfuscation and single-instance enforcement
Ties to AISURU: An Evolution of a Record-Breaking Botnet
High-confidence analysis links Kimwolf to the infamous AISURU botnet (a Mirai variant behind record DDoS attacks). Shared code, infection scripts, signing certificates (e.g., the comical "John Dinglebert Dinglenut VIII VanSack Smith"), and a common downloader server point to the same threat actor. Kimwolf appears to be an upgraded version designed to evade modern Android detections.
Why This Matters to Everyone
Your smart TV or streaming box could be part of this army, quietly launching attacks or serving as a proxy for criminals—without you noticing slowdowns. The holiday season amplifies risks with new gadget purchases.
Broader impacts:
Unprecedented DDoS potential disrupting critical services
Proxy abuse enabling fraud and anonymity for attackers
Exposure of home networks to further breaches
How to Protect Yourself
Buy certified devices: Stick to Google-certified Android TVs; avoid cheap off-brand boxes from untrusted sellers.
Update regularly: Enable automatic firmware updates where possible.
Avoid sideloading: Don't install APKs from unknown sources.
Monitor your network: Watch for unusual outbound traffic.
Factory reset if suspicious: This can remove persistence (though root-level infections may require more).
Segment your network: Keep IoT devices separate from critical computers.
Organizations should block known indicators, monitor for anomalous residential traffic, and share threat intelligence.
The Kimwolf botnet exemplifies how everyday consumer devices are becoming weapons in cyber warfare. As researchers continue monitoring its evolution, staying vigilant is more important than ever.